| |
| |
| Demystifying the Android Malware |
| Author:
Dinesh Shetty |
| |
| |
| |
|
|
|
| |
| |
| |
|
|
| |
| |
|
McAfee's first quarter threat report [Reference
1] stated that with 6 million unique samples of recorded
malware, Q1 2011 was the most active first quarter in malware
history. McAfee stated that Android devices
are becoming malware havens with Android being the second-most
popular environment for mobile malware after Symbian in the first
quarter.
|
 |
|
|
In this article, we will take you through the various phases of
Android malware anlaysis with practical example. To
start with, we will understand the background of Android and then
move on to the basics of how an Android package architecture is
developed. We shall then analyze an Android malware in complete
detail with step by step illustrations. |
|
|
|
|
|
|
|
Android is a mobile-based operating
system based on the Linux kernel. Android application developers write
primarily in the Java language, controlling the device via
Google-developed Java libraries.
The Android compiler suite
compiles the developer's Java files into class files, and then the class
files are converted into dex files. Dex files are bytecode for the
Dalvik VM which is a non-standard JVM that runs on Android applications.
The XML files are converted into a binary format that is optimized to
create small files. The dex files, binary XML files, and other
resources, which are required to run an application, are packaged into
an Android package file. These files have the .apk extension, but they
are just ZIP files. Once the APK package is generated, it is signed with
a developer's key and uploaded onto the Android market via Google's
website from where the user can download these APK files and install
them on the Android device.
There are currently more than 2 million
downloadable applications in the central repository of Android
applications run by Google and android applications can also be
downloaded from other third-party sites. |
| |
| |
| |
- Tool to unpack the .apk file : Winzip
- Tool to convert the .dex to a .jar file : dex2jar
[Reference 2]
- GUI tool for Java decompilation : JD-GUI
[Reference 3]
- Sample Android malware for analysis
|
|
|
|
|
| |
| Here are detailed steps with screenshots
showing each stage of Android malware analysis. |
| |
| |
To start the malware analysis procedure, first
download a sample android malware. In this case, we will download
iCalendar.apk [Reference 4], which was one of the 11 suspicious applications removed
from the Android market because it was found to contain a malware as per
Gadget Media [Reference 5].
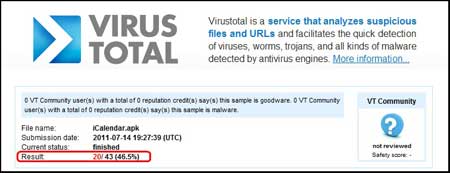
A scan of the application on
VirusTotal [Reference 6] revealed a
detection rate of 46.5% as shown in the figure below. |
| |
 |
| |
| |
| |
| |
Extract the iCalendar.apk file using Winzip to
view the contents of the .apk file. The .dex and the .xml files that
were discussed earlier in the article are shown in below figure.
|
| |
 |
| |
| |
| |
| |
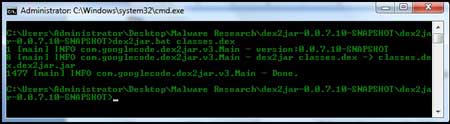
The next step will render a better view of the
code using the 'dex2jar' tool. A dex2jar tool kit converts the Dalvik
executable .dex files into Java .class files.
The 'classes.dex'
file from our application is dropped into the dex2jar's directory and
converted using the command, |
| |
| dex2jar.bat classes.dex. |
|
|
 |
| |
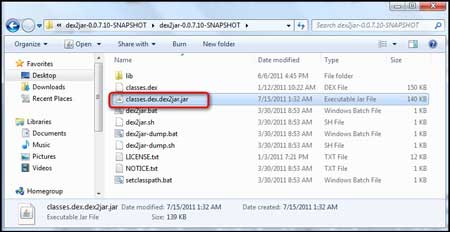
This creates the
'classes.dex.dex2jar.jar' file in the same directory as shown
in below figure.
|
 |
| |
| |
| |
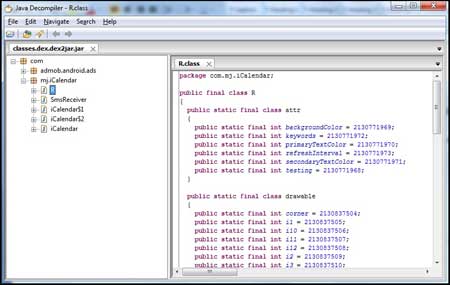
| To view the readable format of the class
files, we use the tool, JD-GUI. Open the 'classes.dex.dex2jar.jar' file
using JD-GUI. |
| |
| |
 |
| |
| This depicts a systematic view of the complete
source code of the Android application. |
| |
| |
| |
After obtaining the complete source of the
application, you can perform the actual analysis of the source and check
whether something is amiss.
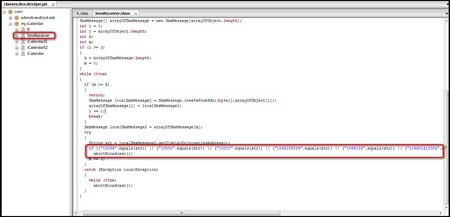
It was observed that the class file named
'SmsReceiver.class' seemed weird as this was a Calendar application and
as the SmsReceiver was not required.
On further inspection of the
source code of the 'SmsReceiver.class', it was found that it contains
three numbers i.e. 1066185829 , 1066133 and 106601412004, which looked
rather suspicious and also looked like there was an attempt to block
messages from these numbers coming to the Android mobile device, which
had this application installed and running. |
| |
 |
| |
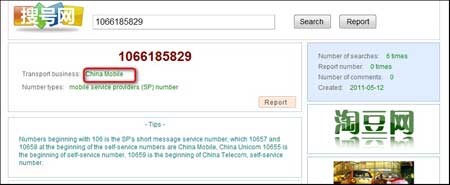
| After searching for these numbers using
Google, it was found that they are high-premium rate SMS numbers that
belong to China Mobile as shown in below figure. |
| |
 |
| |
| We tried to analyze why the application tries
to suppress delivery reports from the above-mentioned numbers in later
steps. |
| |
| |
| |
Once we finished analyzing the
'SmsReceiver.class', we moved on to analyze the code of the next class
file i.e. 'iCalendar.class'.
The first most suspicious thing we
noticed was that, in the showImg() function, after 5 clicks, there was a
call to a sendSms() function. |
|
|
 |
| |
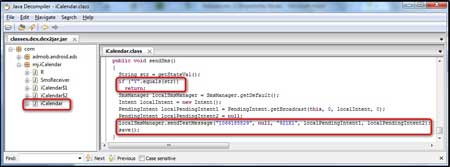
So, we ran though the file and checked for the
'sendSms()' function to see what it does; and Voila!!
As shown in the
figure below, we can see that when the function sendSms() is called, an
SMS is sent to the number 1066185829 with the text 921X1. |
| |
 |
| |
| |
| |
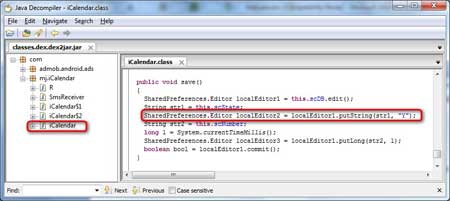
At the end of the sendSms() function, we
noticed that there was a call to the save() function. So, we looked for
the save() function in the code and found it to be just above the
sendSms() function.
|
| |
 |
| |
| After proper analysis and understanding
of the save() function, it was found that the string "Y" is passed
whenever the save() function is called. Also, it was concluded that the
sendSms() function can be called only once and never again due to the
"if" loop that is set for the sendSms() function. |
| |
| |
| |
By combining the results of the entire
analysis, we can obtain a clear picture of the complete functioning of
the malware.
The application sends an SMS
to the premium number 1066185829 with the text 921X1. In the background, it
blocks any
incoming delivery report from this number so that the victim does not
get any response regarding the SMS that the application sends in the
background. Also, the SMS is sent only once and never again so that the
victim has no suspicion of what caused the SMS charges to be sent to
him.
Here is the complete operation cycle of
iCalendar.apk Malware |
| |
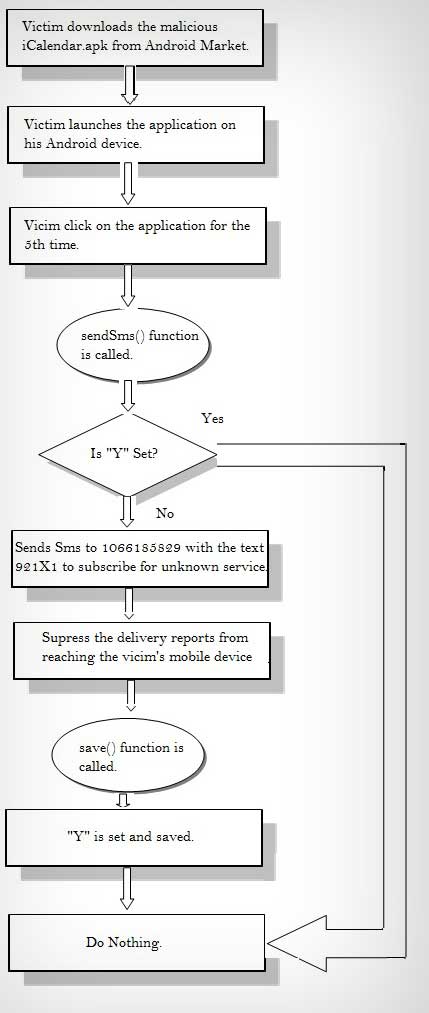 |
| |
| |
| |
| |
A piece of malware with root access to a phone
cannot just read any data stored on it, but can also transmit it
anywhere. This includes contact information, documents, and even stored
account passwords. With access to the root, it is possible to install
other components that are not visible from the phone's user interface
and cannot be easily removed.
Here are some of the ways to safeguard the
application from these Android malwares are: |
- Download applications only from trusted sources.
- Check relevant ratings and reviews before downloading an
application.
- Look at the application's permissions very closely.
- Install Android OS updates as soon as they are available.
- Install a mobile security application.
|
| |
| |
|
-
McAfee's first quarter threat report
- dex2jar: Tool to
convert the .dex to a .jar file
- JD-GUI:
GUI tool for Java decompilation
- Download
Link for iCalendar.apk
-
Infected Android Applications Report
- VirusTotal - Online Virus
Scanner
|
| |
|
This article shows an example of how malwares may affect innocent users.
Without the users actually knowing about it, they are capable of
performing malicious activities in the background.
These
malwares may cause financial losses to the user by debiting call
balances, steal passwords or just corrupt your phone. It is very
important to safeguard the application against these malwares by taking
the necessary precautions.
It is always better to be safe than sorry.
|
| |
| |
| |
|
|
|
| |
| |
| |
| |
| |
| |
| |